Access Systems
CONTROL YOUR COMPANY FROM THE SYSTEM, GIVE AND TAKE ACCESS TO ROOMS OR BUILDINGS ON THE GO
We Listen
Let our staff listen to your technological objectives and create a Security architecture that meets your requirements.
We Design
We will collaborate with you to solve your whole infrastructure, whether large or small. We are one of the best Security Access System companies!
We Integrate
Our team will then assist with the Security build-out, ensuring that your solution is comprehensive and well-managed from start to finish.
What are the types of Access Control Systems?
People can enter a building or area using one of three types of access control systems.
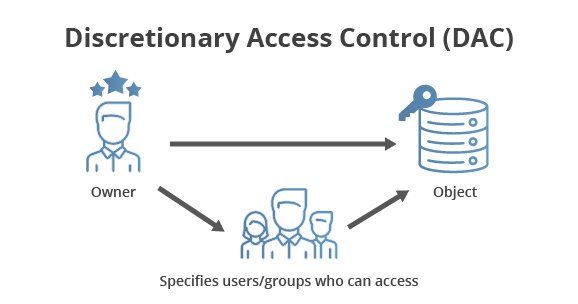
Discretionary Access Control
In discretionary access control systems, the user has complete control over the program and files on the system. It only has one access method, which guarantees access to all doors.
Role-Based Access Control
In role-based access control systems, permissions are determined by a user's position within an organization. The administrator can easily control the system because of its user-friendly interface.
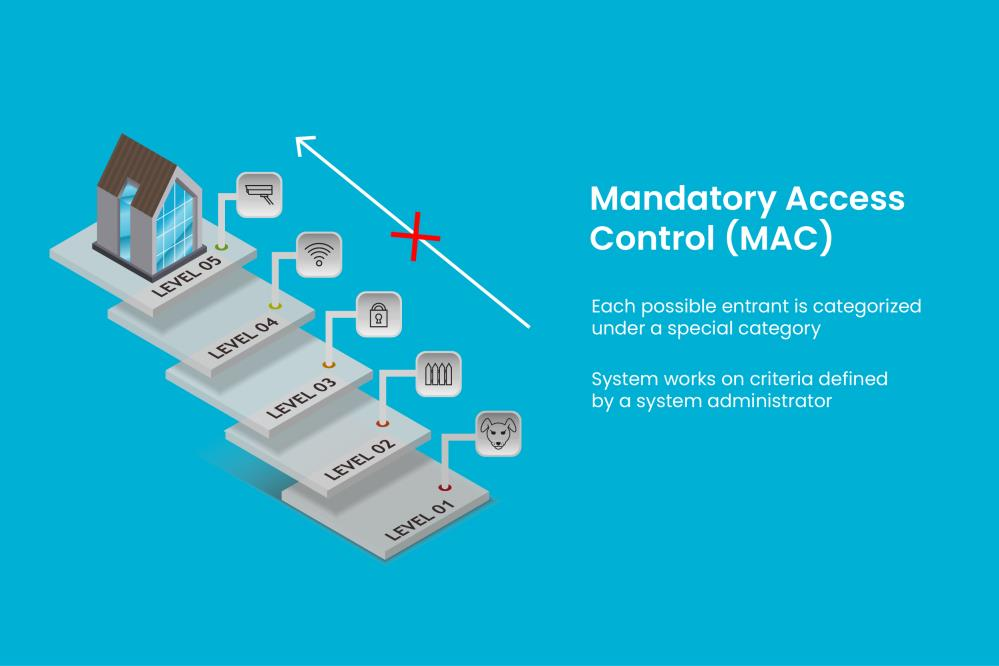
Mandatory Access Control
This is not the same as a control that allows for discretionary access. In mandatory access control systems, a software component, a hardware component, or a policy will be set up to restrict access, typically in the form of a keypad or password.
WHY YOUR BUSINESS NEEDS A DISCRETIONARY ACCESS CONTROL SYSTEM?
You can manage who has access to your house or office building with access control systems. You can secure your or any other premises with locks and keys, but changing locks and reissuing keys can be very inconvenient and expensive if keys are lost or stolen. Additionally, keys can be cloned, increasing security threats.
Systems for electronic access control are the most effective and practical means of protecting your property and its assets. By installing an access control system, whether a rule-based access control system or a mandatory access control system, you can avoid having to change locks ever again. Tokens are given out to allow access through the monitored doors, and if they are misplaced, stolen, or just not returned by a departing employee, they can easily be barred from the system. Barred tokens won't let you through the security doors.
All doors controlled by an access control system will automatically lock once they are closed once it is implemented. No one is permitted entry without a PIN or access token. Doors can be programmed to unlock at specific times if necessary.
All the security services you need, in one place
We have what it takes to help your business prosper
Mandatory Access Control
This is a security architecture in which a central power regulates access permissions based on numerous layers of protection. Designations are commonly used in government and military contexts to allocate to system resources and the operating system or security kernel. MAC permits or refuses access to specific objects according to the user's or device's data security clearance.
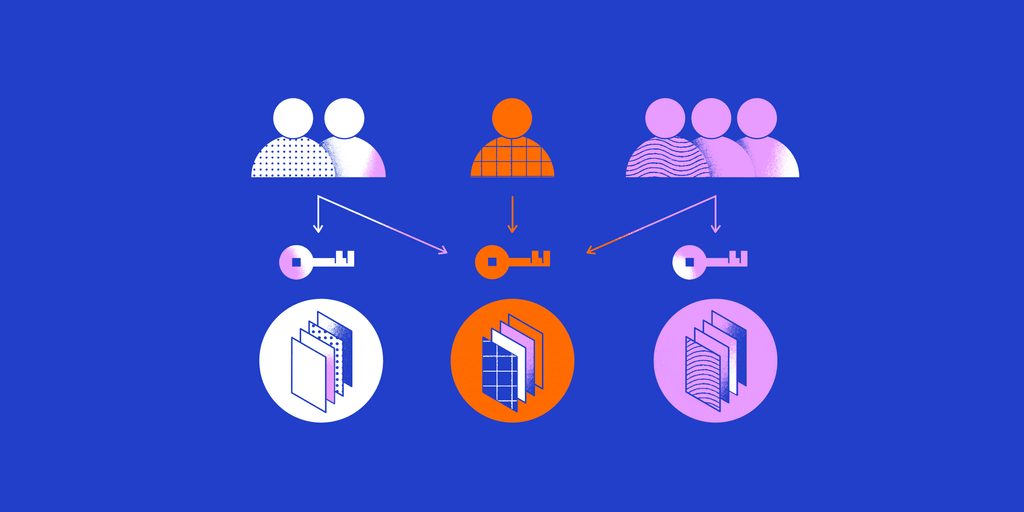
Role-based Access Control
This is a common access control technique that limits accessibility to computing assets based on persons or groups with specified business functions, such as executive level, technician level 1, and so on, instead of single user identities. To govern employee access to systems, the role-based security model depends on a sophisticated framework of role assignments, role approvals, and role permissions built through role engineering.
Discretionary Access control
This is a technique of access control in which the proprietors or managers of the protected network, information, or resource define who or what is permitted to use the resource. Managers can limit the spread of access permissions in many of these technologies.
Rule-based Access Control
The system administrator establishes the rules that control access to resource objects in this security paradigm. These guidelines are frequently dependent on environmental factors such as time of day or location. It is not uncommon for access regulations and processes to be enforced using a combination of rule-based access control and RBAC.
Your Ideas Are Real
The safety and security of your commercial properties are an everyday concern. Whether you run a huge corporation, it is essential to safeguard your assets, personnel, information, and building against external threats as well as any internal problems that can arise. And this does not stop with only commercial activities; your home also needs to be secured from break-ins and unauthorized access. You can regulate who enters your house or office or secured sections within it by installing an access control system, which also offers integration with your video surveillance and other building management systems.
At LOWVO, we think every commercial property needs to be protected. LOWVO can assist you in designing and installing an access control system that makes use of advanced hardware and the most recent technology developments. Access control solutions from LOWVO can be created to fit any budget. LOWVO has a solution to fit your demands. So, whether you want an access control system for your residence or a high-end access control system for your office, LOWVO offers solutions tailored according to your specific needs!
What Features LOWVO's Access Control Systems Has To Offer?
- It offers account protection by RSA and AES encryptions in the TCP/IP system framework.
- It offers a variety of access options, including biometrics, card token, password, and combinations.
- It offers multiple alarm options that can be programmed to buzz when any specific events take place.
- It offers multi-system interconnection, including fire alarms, P.O.S, HVAC, and video surveillance.
- It offers physical and remote access to instantly lock all doors across the premises.
- It offers a user-friendly mobile application for security notifications and allows you to lock any premises instantly.
- It offers integrated attendance solutions to minimize your hassle.
More LOWVO Services
Structured Cabling
With our installation, you’ll save time when you need it most. It’s the organized way to meet your customers’ needs quickly...
Fiber Optics
You’ll enjoy company growth faster than you expected possible, by streamlining services and features...
Fleet GPS Installation
Truck GPS tracking solutions automate data gathering and documentation in the field and on the road, sparing operators time and reducing mistakes. Fleet managers may use these solutions to obtain real-time fleet performance information on the go...
Point Of Sale
With our POS you will enable beneficial management technology. Be able to manage your gross earning all at a swipe with...
Digital Signage
You’ll enjoy company growth faster than you expected possible, by streamlining services and features.
Security Systems
Our security team is available every day to make sure that things runs smoothly. We’re here to help.
Why LOWVOs choose us to install access control systems?
The safety and security of your residential as well as commercial properties are an everyday concern. Whether you run a small home-based business or a huge corporation, it is essential to safeguard your assets, personnel, information, and building against external threats as well as any internal problems that can arise. And this does not stop with only commercial activities; your home also needs to be secured from break-ins and unauthorized access. You can regulate who enters your house or office or secured sections within it by installing an access control system, which also offers integration with your video surveillance and other building management systems.
At LOWVO, we think every residential or commercial property needs to be protected. LOWVO can assist you in designing and installing an access control system that makes use of advanced hardware and the most recent technology developments. Access control solutions from LOWVO can be created to fit any budget. LOWVO has a solution to fit your demands. So, whether you want an access control system for your residence or a high-end access control system for your office, LOWVO offers solutions tailored according to your specific needs!
Request
A Free Quote
Get a cost-effective IT plan that is tailored to your specific needs. With our personalized solution, you will only receive what you require and nothing else
Request your FREE Quote
We will get back to you as soon as possible
Please try again later

The LOWVO team has over 25 years of experience with the installation of many different types of cabling. We’re one of the pioneers of structured cabling; we have grown with the industry trends as the world has expanded it’s needs and demands on providing the fastest and most effective wired and wireless network infrastructures at the enterprise level. No structured cabling project is too small or large!
LOWVO is committed to designing, developing and deploying reliable structured cabling solutions that support your infrastructure’s data, video and telephony connectivity.
Let’s change products for Business Solutions, remember we don’t sell Internet Services, we sell cabling services and network services
Navigation
Business Inquires
Join the Newsletter
We will get back to you as soon as possible
Please try again later
All Rights Reserved | Website Design By Kansas City Business Operations